Nobody is sure how the hackers gained access to Colonie’s system on Wednesday, Jan. 15 — and it may never be determined with any degree of certainty — but the working presumption is that it was through an innocent employee opening an innocent looking attachment that came via an innocent looking email.
Town Attrorney Michael Magguilli said the working hypothesis is the attack came from Russia and the same type of virus used to attacked Albany International Airport but “I don’t think anyone knows that 100 percent.”
The head of the town Management Information Services, Lisa Travis, said she wasn’t sure if anything drastic will change in how Colonie protects its data but conceded the “attackers get smarter and smarter and the viruses get stronger and stronger so it [security] is a continual process.”
Click here to read how Colonie fought back against the hackers
“Everyone has some holes and you don’t realize it until you are in that situation so we are continually testing and making sure data is secure,” she said. “We have some severs patched and we are hitting employee education pretty hard to make sure people recognize that in the year 2020 you can’t open everything that comes to you.”
 Colonie and the Capital District not alone. According to the FBI, the number of ransomware and/or other types of cyberattacks are getting more pervasive and no one is 100 percent immune. It is so pervasive, the FBI urges anyone victimized by such hackers to let them know, said Public Affairs Specialist Sarah Ruane. There is a website established just so people can report cybercrimes called IC3, which stands for Internet Crime Complaint Center, and can be accessed at ic3.gov. Or, she said, call the local FBI field office to report the attack.
Colonie and the Capital District not alone. According to the FBI, the number of ransomware and/or other types of cyberattacks are getting more pervasive and no one is 100 percent immune. It is so pervasive, the FBI urges anyone victimized by such hackers to let them know, said Public Affairs Specialist Sarah Ruane. There is a website established just so people can report cybercrimes called IC3, which stands for Internet Crime Complaint Center, and can be accessed at ic3.gov. Or, she said, call the local FBI field office to report the attack.
Reporting directly to the FBI is a break from decades long protocol of advising people to “contact your local law enforcement agency” of any suspected crimes because cybercrime is so widespread, is happening across all jurisdictions and borders and is costing billions of dollars a year.
“The sooner we can be made aware of the cyberattack the sooner we can help and get in and retrieve the information we need,” Ruane said. “All of those complaints are taken in, studied by analysts and distributed to the right region and we try to establish trends and see if one area is more susceptible than another at any given time.”
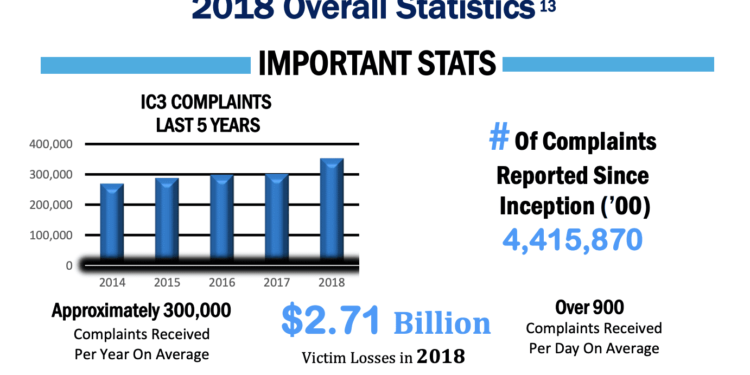
In 2018, the most recent full year of data, according to the Internet Crime Report, the FBI received about 350,000 complaints via the IOC3 website and it is estimated cybercrime cost victims about $2.7 billion.
According to the 2018 report, the most prevalent type of cybercrime, with 65,116 victims, was “non-payment, non-delivery. That was followed by 51,146 incidents of extortion, 50,642 incidents of data breach and 26,379 phishing viruses.
New York state had the fourth most complaints filed in 2018 with 18,124 victims but placed second in total losses at $201 million, according to the FBI report. California had the most number of complainants, 49,031 and it cost them the most, $450 million.
“We expect 2019 numbers will be staggering,” Ruane said. “And these are just the people who take the time to report it. We think there are a great deal of people who just fix it on their own and move on.”
The hackers are extremely difficult to catch and harder to prosecute. The perpetrators often live in different countries, outside the jurisdiction of the U.S. legal system, and evidence can be eliminated with a key stroke.
As such, preventing a cyberattack is the ideal method of fighting one. Ransomware, like what afflicted Colonie’s computer, is the preferred mode when the victim is larger with deeper pockets and has more than one server. Individuals, though, are also susceptible to cyberattacks with the worst case scenario being someone hijacking personal information like bank accounts or credit card numbers.
“We are seeing a huge influx of these types of attacks and we are realizing not enough people know about it or how to prevent it,” Ruane said. “It is so much easier to prevent than to try and deal with it once it is allowed into a system or a computer.”
Some tips from the FBI include:
• While ultimately it is the victim’s choice, the FBI strongly recommends not paying a ransom. It emboldens the hackers and often times does not allow the access to data and quicker or at all. And, there is often no guarantee the hackers won’t lock down the system again and demand more money
• Corporations should have a backup that is separate and distinct from the main server for data and update the backup data with fresh data as often as possible.
• Have an incident response plan in place before something happens to get the system back up and running as soon as possible.
• Do penetration testing, or hacking into your own system to test the security and see where there might be holes.
• Hire a consultant to help navigate what is a complex and constantly changing world.
• Individuals should also have a backup off line on something like a flash drive or an external hard drive so if they are hit, they can wipe and rebuild their own machine. A cloud based backup system or anything connected to the internet does not do any good.
• Pay attention to emails and if something looks fishy don’t open it.
• Proper training can help employees recognize what emails and other online sites to avoid.
• If your computer or system is infected, notify the FBI as soon as possible.
• Simple things like keeping anti-virus, firewalls and operating systems up to date, turning off a computer when not in use and watching what you download.
• Companies should hire in house professionals or contract with reputable companies to design systems and backups. Or, hire a consultant to find the right company to build the system to the desired specifications.
• Consumers should be aware of strange emails or invites to open a link because if it is a virus, once it is clicked it will take over your data.
• Use complex passwords and don’t keep the passwords to bank accounts or other sensitive data on the same computer you use to access the data.
• Consumers should use common sense and take heed of the old adage: “If it’s sounds too good to be true, it usually is.” In other words, the ads selling brand new products at deep discounts could be fake and only exist to get hold of your credit card number.
“One of our agents told me that if you went to Best Buy and you saw some shady guy in the corner of the parking lot selling the $400 product for $40 you wouldn’t do it,” Ruane said. “Consumers have to have that same mentality for what they see online.”